
Helm Bank USA

Prevent Email Spoofing and Wire Fraud
Do you know what's in your email inbox?
Some dangerous messages from scammers may be sent to your inbox in an attempt to convince you to wire money to them, all while acting as legitimate companies or individuals. This practice, known as email spoofing, leads to financial damage for targeted companies or individuals and increases stress for everyone involved. Know the signs of email spoofing to safeguard your personal and corporate accounts.
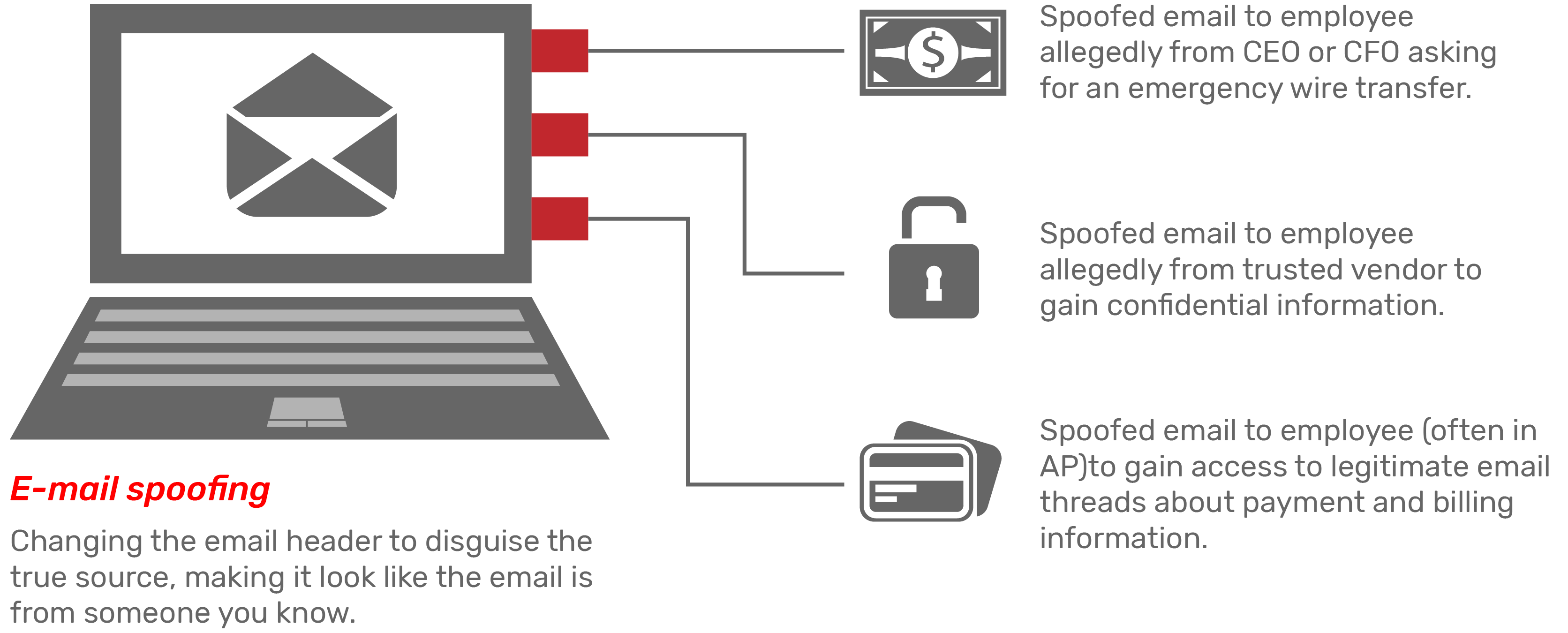
How Email Spoofing Works:
The organized criminal groups that engage in business e-mail compromise scams are incredibly sophisticated.
- Spoofing e-mail accounts and websites: Slight variations on legitimate addresses (@HemlBankUSA.com vs. @HelmBankUSA.com) deceive victims into thinking fake accounts are authentic. The criminals then use a spoofing tool to direct e-mail responses to a different account that they control.
- Spear-phishing: Fake e-mails believed to be from a trusted sender prompt victims to reveal confidential information to the Business Email Compromise (BEC) perpetrators.
- Malware: Used to infiltrate company networks and gain access to legitimate e-mail threads about billing and invoices. Malware also allows criminals undetected access to a victim’s data, including passwords and financial account information.
Don’t Be a Victim
The business e-mail compromise scam has resulted in companies and organizations losing billions of dollars. But as sophisticated as the fraud is, there is an easy solution to thwart it: face-to-face or voice-to-voice communications. Instead of relying on email alone, the best way to avoid being exploited is to verify the authenticity of any requests to send money is to speak to the person directly on the phone.
Here are other methods businesses have employed to safeguard against Business Email Compromise (BEC):
- Create intrusion detection system rules that flag e-mails with extensions similar to company e-mail. For example, legitimate e-mail of abc_company.com would flag fraudulent e-mail of abc-company.com.
- Create an e-mail rule to flag e-mail communications where the "reply" e-mail address is different from the “from” e-mail address shown.
- Color code virtual correspondence, so e-mails from employee/internal accounts are one color and e-mails from non-employee/external accounts are another.
- Add additional two-factor authentication to verify changes in vendor payment location, such as having secondary sign-off by company personnel.
- As a part of two-factor authentication, use phone verification to confirm requests for transfers of funds; use previously known numbers, not the numbers provided in the e-mail request.
- Carefully scrutinize all e-mail requests for transfer of funds to determine if the requests are out of the ordinary.

